Microsoft requires you to be a Global Administrator or a Billing Administrator if you want to purchase any subscription within Office 365. This holds true no more!
Starting 14 January 2020, Microsoft is giving this control to end-users for its Microsoft Power Platform which currently has three apps - PowerBI, PowerAutomate (Flow) and PowerApps. With this change, the end-users can really 'Self-Purchase' the subscriptions for these three apps as well as the new apps which will get launched under Power Platform in future.
Starting 14 January 2020, Microsoft is giving this control to end-users for its Microsoft Power Platform which currently has three apps - PowerBI, PowerAutomate (Flow) and PowerApps. With this change, the end-users can really 'Self-Purchase' the subscriptions for these three apps as well as the new apps which will get launched under Power Platform in future.
For now, this change only applies to the Power platform and not other traditional plans like E1/E3/E5.
While this change can make it easier and faster for your users to access and consume Power platform apps like PowerBI Pro a faster, it can significantly swell your bills as users may start purchasing service they don't necessarily need, or business won't approve for everyone.
Don't worry, it's not too late. You CAN turn this OFF so things go back to normal once again. You'd need to run the following PowerShell Cmdlets -
As of today, you see three products - Power Apps, Power BI Pro and Power Automate based on the subscriptions your tenant has.
Above code disables ALL services at the same time. If you prefer disabling only one service at a time, you can use a line similar to below for 'Power Automate'
Once this cmdlet is run you can see the change by running cmd from step 2 again -
Don't worry, it's not too late. You CAN turn this OFF so things go back to normal once again. You'd need to run the following PowerShell Cmdlets -
Step 1. Install PowerShell Module "MSCommerce"
Import-Module -Name MSCommerce
Connect-MSCommerce

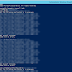
Step 2. Check how your tenant is currently set for these new controls
Get-MSCommerceProductPolicies -PolicyId AllowSelfServicePurchase
As of today, you see three products - Power Apps, Power BI Pro and Power Automate based on the subscriptions your tenant has.
Step 3. Disable the Self-Service Purchase Options for your subscriptions
Import-Module -Name MSCommerce
Connect-MSCommerceGet-MSCommerceProductPolicies -PolicyId AllowSelfServicePurchase | Where { $_.PolicyValue -eq “Enabled”} | forEach {Update-MSCommerceProductPolicy -PolicyId AllowSelfServicePurchase -ProductId $_.ProductID -Enabled $false }Above code disables ALL services at the same time. If you prefer disabling only one service at a time, you can use a line similar to below for 'Power Automate'
Update-MSCommerceProductPolicy -PolicyId AllowSelfServicePurchase -ProductId CFQ7TTC0KP0N -Enabled $False
Once this cmdlet is run you can see the change by running cmd from step 2 again -